Stingray
Stingray

Image Gallery
Cell site simulators are often called “Stingrays,” after the name given to the most popular model on the market. These tools track the locations of wireless mobile devices such as cell phones, mobile tablets, and wireless broadband cards. Police use some models to intercept calls, text messages, or emails sent between different devices. If the government knows which phone to look for, a Stingray can pinpoint its location. However, it collects location data indiscriminately from all the nearby devices that are associated with the particular network the Stingray is impersonating. These devices transmit signals into all nearby homes, cars, bags, and pockets, looking for every device in the area that connects to that network. Police can use it to find out every person in a particular place at a given time, raising serious privacy concerns.
CIVIL LIBERTIES CONCERNS
Stingrays are indiscriminate – they enable law enforcement to determine the location of not only individuals suspected of criminal activity, but potentially tens of thousands of people at once.
Ensuring accountability for law enforcement use of this technology is challenging. Under pressure from Harris Corporation, the most popular manufacturer, many federal agencies and local police departments have refused to provide technical details about the design and function of Stingrays. Some have even signed non-disclosure agreements barring them from confirming or denying that they have bought or leased them. Thus, these devices have been used in secret and have collected information from large numbers of law-abiding people.
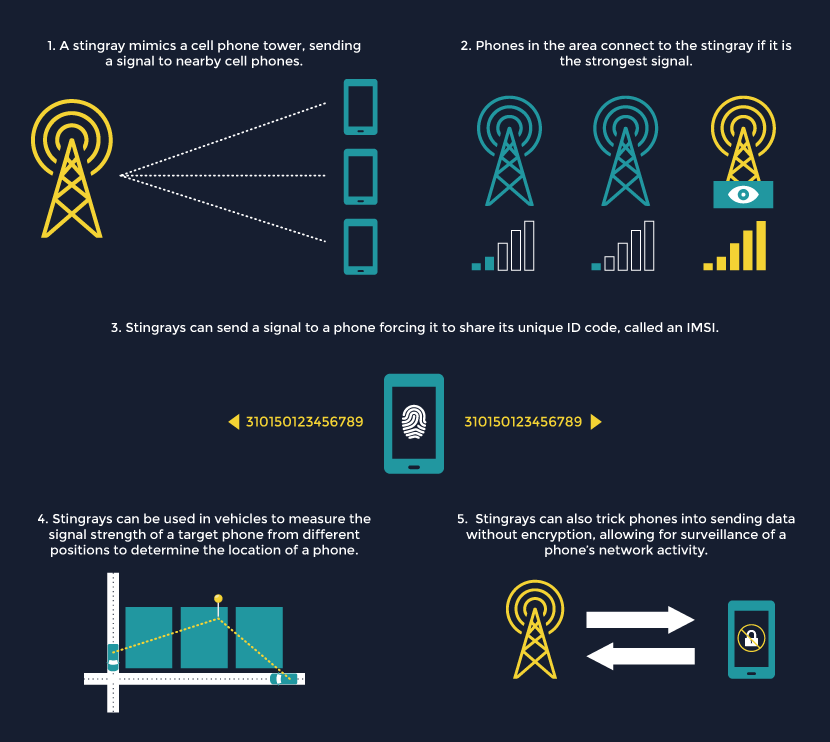
Stingrays imitate cell towers in order to figure out the location of wireless devices.
- Several times a minute, your cell phone sends a signal with a unique identifier that connects it to a nearby cell tower. Every mobile network user has a unique International Mobile Subscriber Identity (IMSI), represented by a 12- to 15-digit number. Your cell phone probably carries this number in its SIM card.
- The Stingray deceives cell phones by imitating a cell tower. It entices all mobile phones and wireless broadband cards within range of the device to connect. Once these connections are established, they enable the operator to collect all sorts of sensitive information.
- Usually, the Stingray collects location data. When targeting a particular mobile user, police use the Stingray to measure the signal strength of the user’s phone to estimate the distance between the two devices. After doing this from several different locations, the Stingray uses the data to triangulate the precise location of the target device. However, the device connects to all phones in range. That means that is can identify and track the movements of all mobile users within a particular area at a particular time. Harris Corp. boasts that one advanced model, the “Triggerfish,” tracks the IMSIs of up to 60,000 phones at a time.
- Even more troubling, later-generation models can intercept and extract usage information from any device it connects to. Police using this type of Stingray can read your Internet search history, text messages, call records, and even listen to your phone calls. In some cases, these devices may even be capable of delivering malicious software, or spyware, to personal devices.
Secrecy surrounds these devices. However, public records confirm that federal agencies including the FBI, DEA, and IRS have acquired and used them in criminal investigations. In fact, Justice Department documents have revealed that federal agents sometimes neglect to inform federal judges that they intend to use Stingrays when seeking authorization to recover phone location data. Additionally, privacy advocates have confirmed Stingray use by local police in Arizona, California, and Florida. The ACLU found that the Tallahassee Police Department used its Stingray over 200 times without ever asking for a warrant from a judge.
Examples of Use
When government agencies consider acquiring and using surveillance systems, communities and their elected officials must both weigh the benefits against the costs to civil liberties and carefully craft policies and procedures that help to limit the negative effects that surveillance will have on fundamental rights. For a useful list of considerations, please visit the recommendations page.