Image Gallery
Powerful computer programs analyze images of human faces and compare them against photographs stored in government databases. After 9/11, airports and sports stadiums began using the technology to compare travelers and fans against the images of known or suspected terrorists. As mass video surveillance becomes more widespread, local police have begun using the technology to catch ordinary criminals.
CIVIL LIBERTIES CONCERNS
Without legal safeguards, the government could use it to identify involved in lawful activities, such as protest marchers, reproductive clinic patients, or gun show patrons. Further, huge facial image databases are available to police and government agencies and extremely vulnerable to abuse. Most departments store their mug shot banks electronically, allowing police to compare faces captured on camera to past offenders. However, many police officials are pushing for access to larger, non-criminal photo banks, such as driver’s license photos. This raises significant privacy and abuse concerns, since it substantially expands the potential for use of those photos for dragnet surveillance purposes. This allows video surveillance operators to place you at a particular place and times. As the ubiquity of video surveillance increases, so does the ability of surveillance operators to track your movements and to engage in fishing expeditions.
In the past, facial recognition systems have returned large numbers of both false positives and false negatives. In 2003, Boston’s Logan Airport shut down its facial recognition program after it failed to identify a single person in two years. But recent advances in video quality and identification software, along with access to enormous government image banks, have overcome many of the early systems’ technical drawbacks.
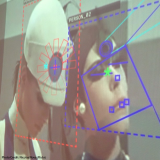
- Facial recognition algorithms analyze images for unique facial features. They inspect the size, shape, and position of our noses, eye sockets, cheekbones, and jawbones. Some even read our skin color and texture. These features single us out from others, even our closest relatives.
- A facial recognition program converts its analysis of a face captured on camera into a data set. It then looks for a similar data set stored in a police database. Ideally, it matches a face already contained in an index of mug shots. However, the technology is far from perfect. Getting a match is no guarantee that the correct person has been identified.
- Facial recognition technology has gone mobile. Dozens of cities and counties from Massachusetts to Arizona use the Mobile Offender Recognition and Information System (MORIS). This handheld, battery-operated device scans the face or iris of a suspect and compares the scan to a police database. It then instantly transfers ID and criminal history information to the officer’s smart phone or laptop.

Facial recognition software has become very powerful, user-friendly, and less and less expensive. Moreover, handheld facial recognition tools give officers easy access to this intrusive technology. In 2011, Ohio announced that it would become the 27th state to use its driver’s license photo bank as a “law enforcement fishing pond.” In addition, this year, the FBI announced plans to build a database of 52 million facial images by 2015. Each image will match a “name, home address, ID number, immigration status, age, race, etc.” Troublingly, many of the FBI’s records are non-criminal. If your job requires a background check at hiring, your image may be searchable in this database. Over half of all U.S. states plan to take part in this massive data-sharing project.
Examples of Use
When government agencies consider acquiring and using surveillance systems, communities and their elected officials must both weigh the benefits against the costs to civil liberties and carefully craft policies and procedures that help to limit the negative effects that surveillance will have on fundamental rights. For a useful list of considerations, please visit the recommendations page.