Deep Packet Inspection

Image Gallery
Deep packet inspection allows the government to review the online communications of a suspect or target of investigation as those communications are moving through the network. Deep packet inspection tools access, scan, and even copy the entire contents of your email, web browsing, posting, and shopping.
CIVIL LIBERTIES CONCERNS
Private companies and government agencies can use this technique to secretly watch users and restrict their online activities. As PC World notes, “in the absence of strict legal restrictions, your ISP can root through the information you exchange and use it as they see fit. Personal information like your age, location, and shopping habits can be sold in anonymized batches to advertising companies” or passed on to law enforcement. The NSA and the FBI have tapped directly into these data streams. This allows them keep tabs on your activities without asking your ISP. An agency could use the same tools to block certain users or sites altogether. Some foreign governments restrict access to certain websites using packet inspection tools.
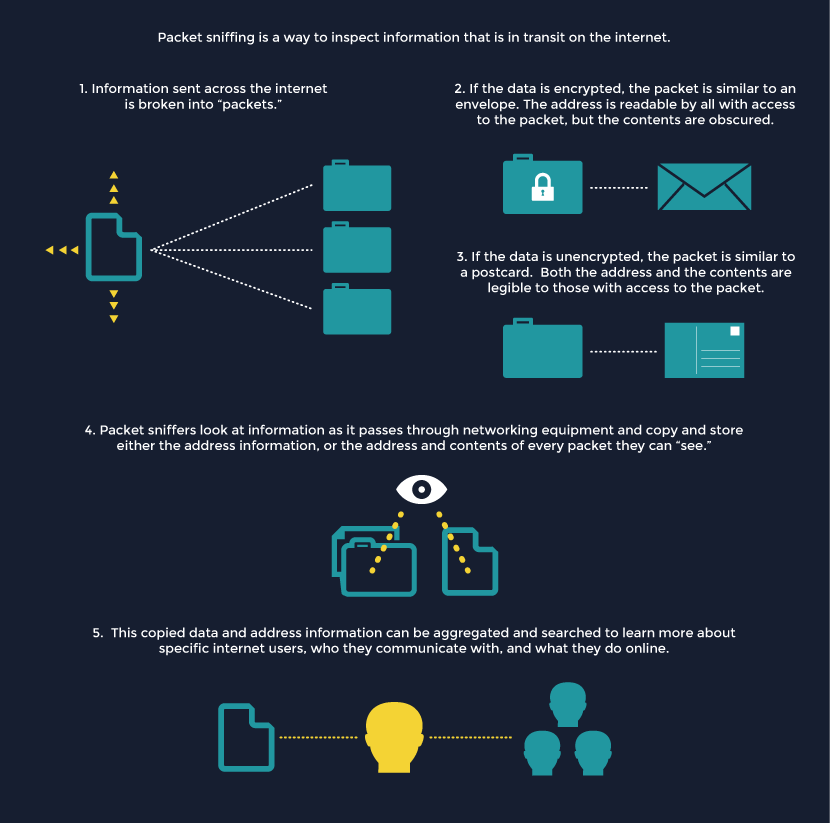
- Computers transmit all of the information you send and receive online in the form of data clumps called “packets.” Every web page you open and email you send is broken down and sent through the network as a series of packets that are rebuilt at their destination.
- Internet service providers use “shallow” packet inspection to analyze a small part of the packets in order to route internet traffic and protect users. The “labels” on data packets enable internet routing systems to figure out who sent them, who should receive them, and how they should be put back together at their destination. Internet service providers similarly conduct some form of packet “sniffing” to protect users from spammers and other online troublemakers. Usually, this involves reading the “labels” on data packets to determine where the data is coming from.
- “Deep packet inspection,” however, scans and logs the entire contents of data packets. Using this technique, police or intelligence agents investigating a criminal suspect can inspect all of that person’s unencrypted internet traffic. In theory, an agency could simply copy everything that passes through a network.
Government agencies tend to be secretive about their use of advanced surveillance technologies, and we don’t know how many agencies use this technique. Deep packet inspection requires some technical skill and, more importantly, access to the networks of private internet companies. So, few state and local police departments currently engage in it. Probably, only the best-funded national agencies currently use deep packet inspection, though perhaps the police departments of large states or major cities could do so as well.
Examples of Use
When government agencies consider acquiring and using surveillance systems, communities and their elected officials must both weigh the benefits against the costs to civil liberties and carefully craft policies and procedures that help to limit the negative effects that surveillance will have on fundamental rights. For a useful list of considerations, please visit the recommendations page.